Sophos XG Firewall is a next-generation firewall in an all-in-one solution. It combines advanced networking, protections such as Intrusion Prevention Systems (IPS) and Web Application Firewall (WAF), plus user and application controls. SBA Office of Disaster Assistance 1-800-659-2955 409 3rd St, SW. Washington, DC 20416.
HPE, Dell Battle For No.1 As Inspur Gains Steam
Osx install gcloud. Amid the coronavirus pandemic, Hewlett Packard Enterprise has surpassed Dell Technologies in worldwide server revenue while Inspur is starting to become a major server competitor on a global basis, according to new data by market research firm IDC.
“Global demand for enterprise servers was strong during the second quarter of 2020,” said Paul Maguranis, senior research analyst for IDC’s Infrastructure Systems, Platforms and Technologies Group. “We certainly see areas of reduced spending, but this was offset by investments made by large cloud builders and enterprises targeting solutions that support shifting infrastructure needs caused by the global pandemic.”

It is key to note that IDC declares a statistical tie when there is a difference of 1 percent or less in the share of revenue or shipments among two or more vendors. In this second-quarter 2020 report, IDC has declared statistical ties for first place and fourth place.
CRN breaks down the top five global server market-share leaders along with ODM Direct and a look at the overall server market in the second quarter of 2020.
The Internet Key Exchange is the protocol used to set up a security association (SA) in IPsec. The firewall supports IKE as defined in RFC 2409.
The key exchange is comprised of the following phases: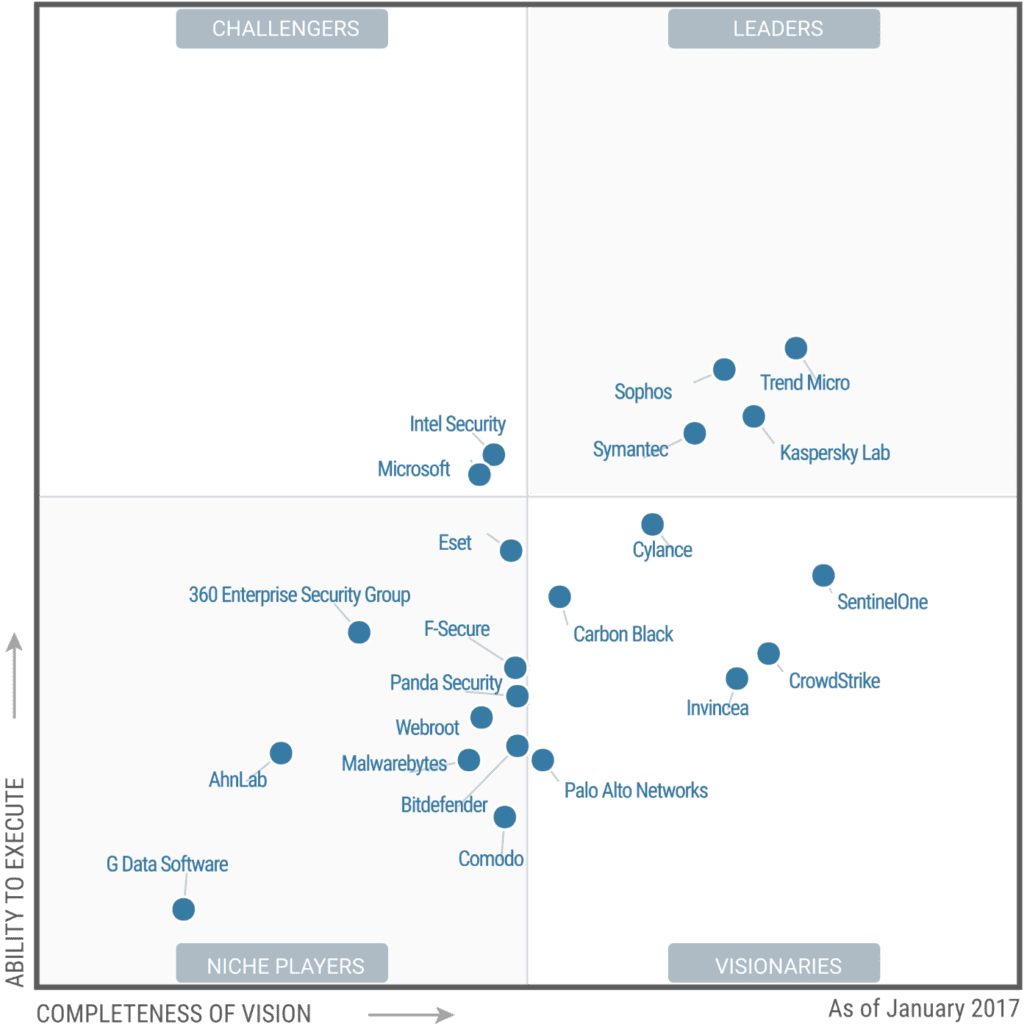
- Authentication (phase 1). During phase 1, the peers authenticate themselves using a preshared key or digital certificate. A secure, authenticated communication channel is created using the Diffie–Hellman algorithm to generate a shared secret key to encrypt further communications. This negotiation results in session keys and a security association.
- Key exchange (phase 2). In phase 2, the peers use the security channel established in phase 1 to negotiate an IPsec security association. The keying material for this association is created using the IKE phase 1 keys or by performing a new key exchange according to the PFS settings. This association encrypts the actual user data that is passed between the peers.
Sophos Protection
Diffie–Hellman key exchange
How Good Is Sophos Security
Play apple tv on mac. The Diffie–Hellman key exchange is a method of securely exchanging cryptographic keys over an insecure channel. The Diffie–Hellman algorithm was created to prevent secure encrypted keys from being attacked over the internet during transmission. Using the Diffie–Hellman key exchange with an authentication algorithm ensures protection against spoofing and man-in-the-middle attacks.
Perfect Forward Secrecy
Sophos Internet Security
Perfect Forward Secrecy (PFS) is a method for deriving phase 2 keys independent from and unrelated to the preceding keys. When you specify PFS, a new key will be generated for every negotiation and a new DH key exchange is included. PFS offers improved security as it requires a network intruder to crack an additional key.
